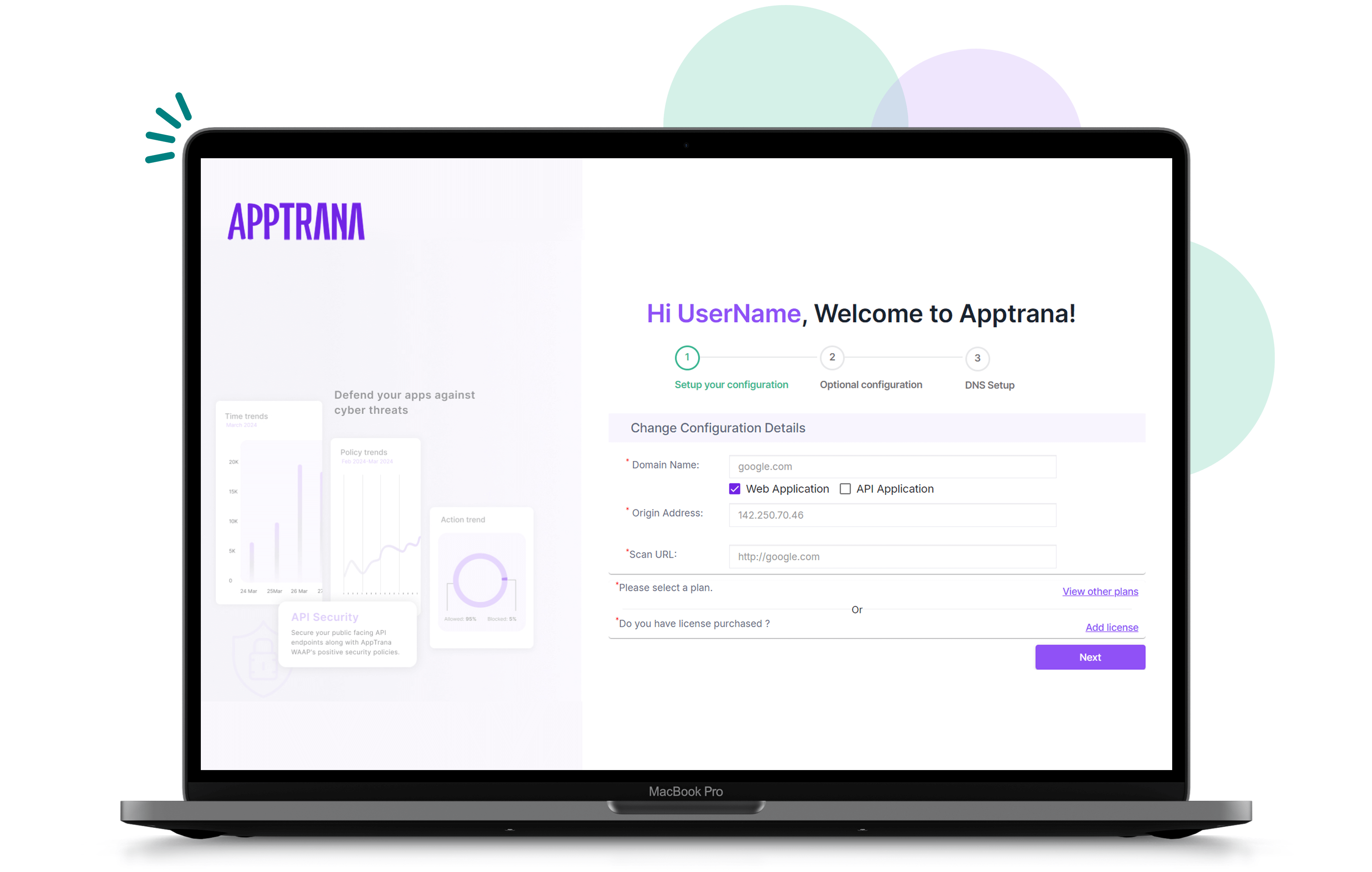
Complete security solution for your applications and APIs
Autonomous virtual patches fix web and API flaws instantly. Cut patch times from 200+ days to near real time.
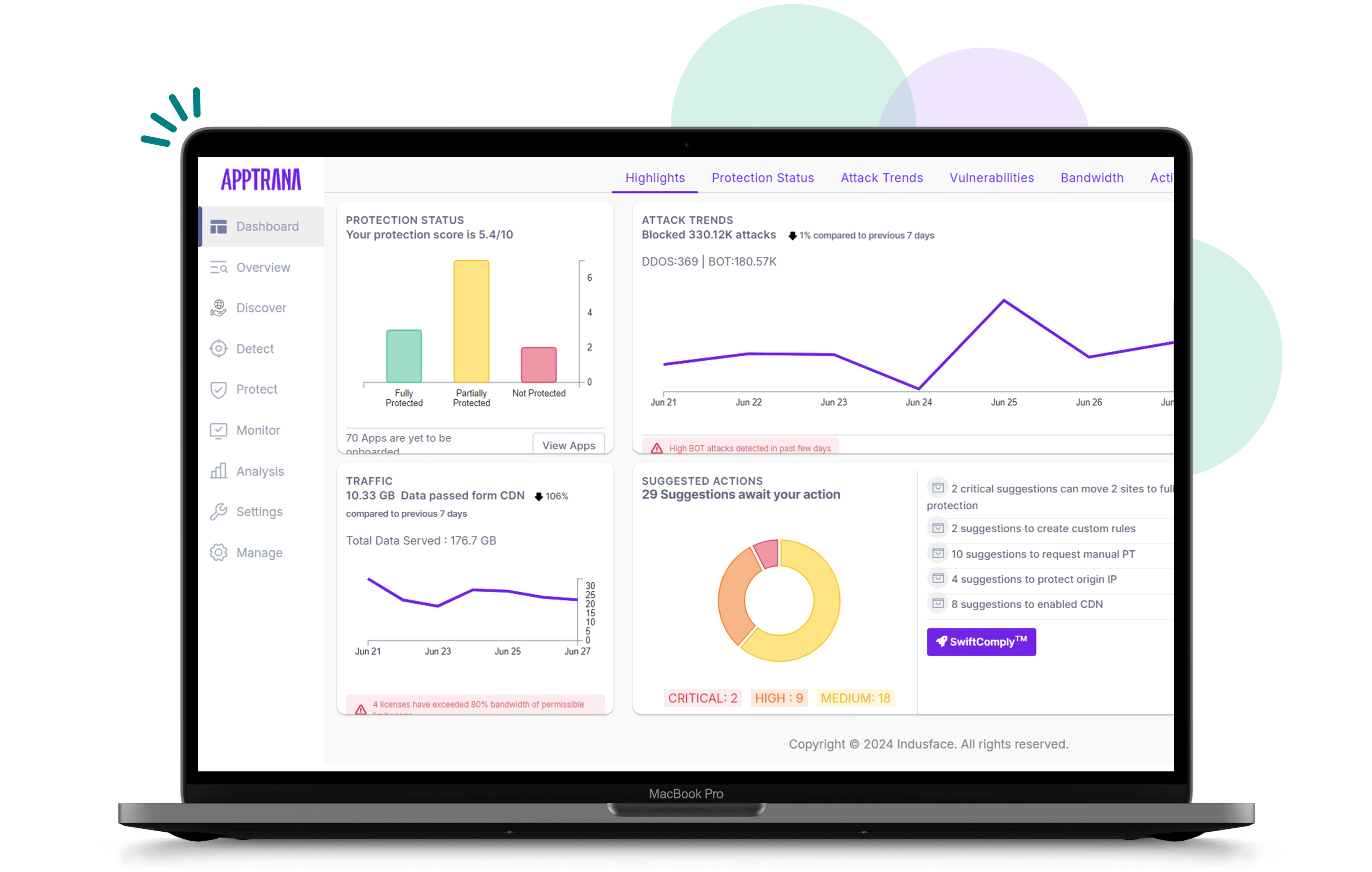
All-in-one, AI-powered platform for attack surface management, vulnerability management and web app and API protection
100 % uptime SLA backed by behavioral DDoS and bot mitigation, monitored round-the-clock by a 24/7 SOC.
DNS management and protection against DNS hijacking and tunneling and other DNS attacks.
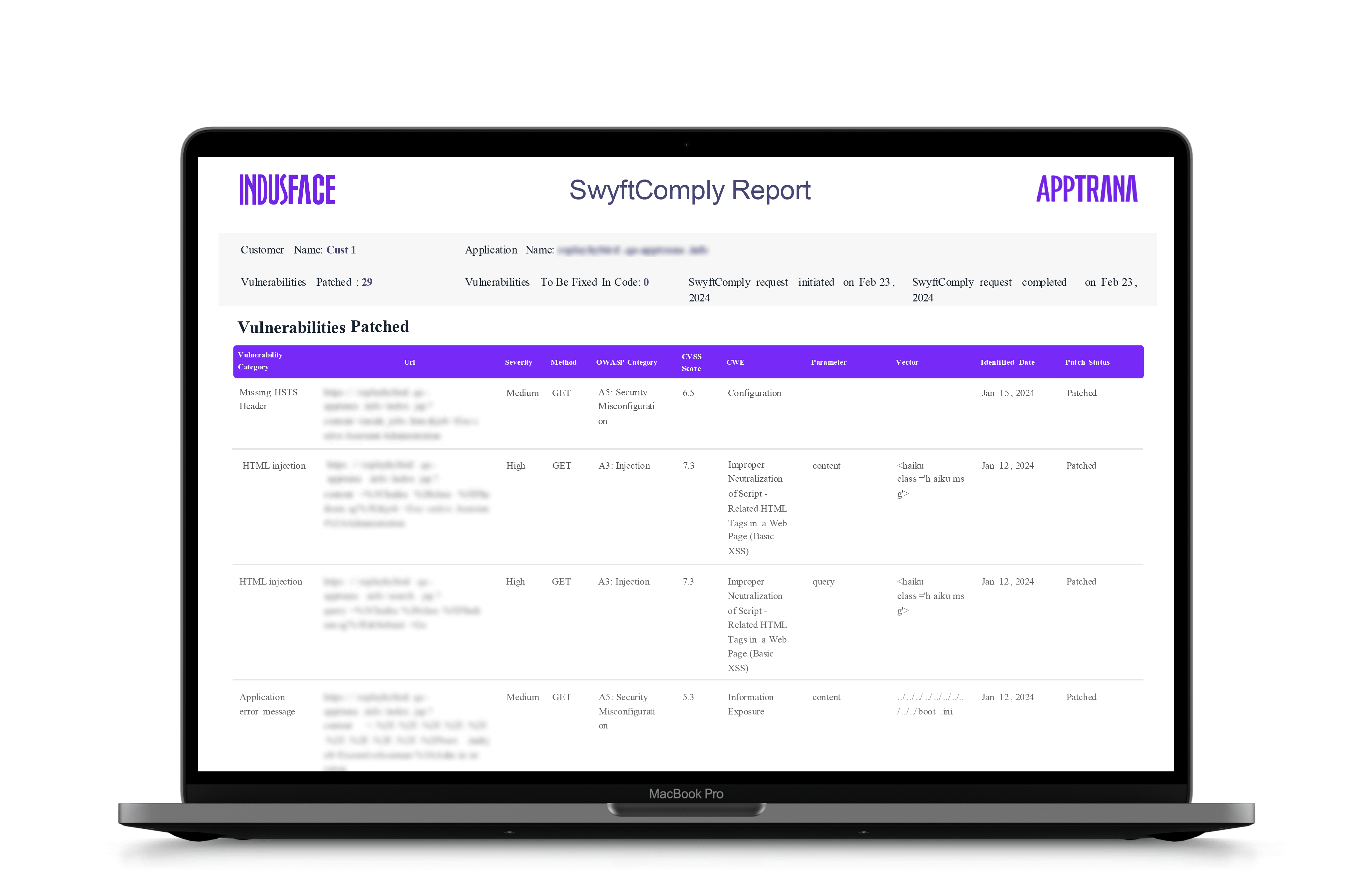
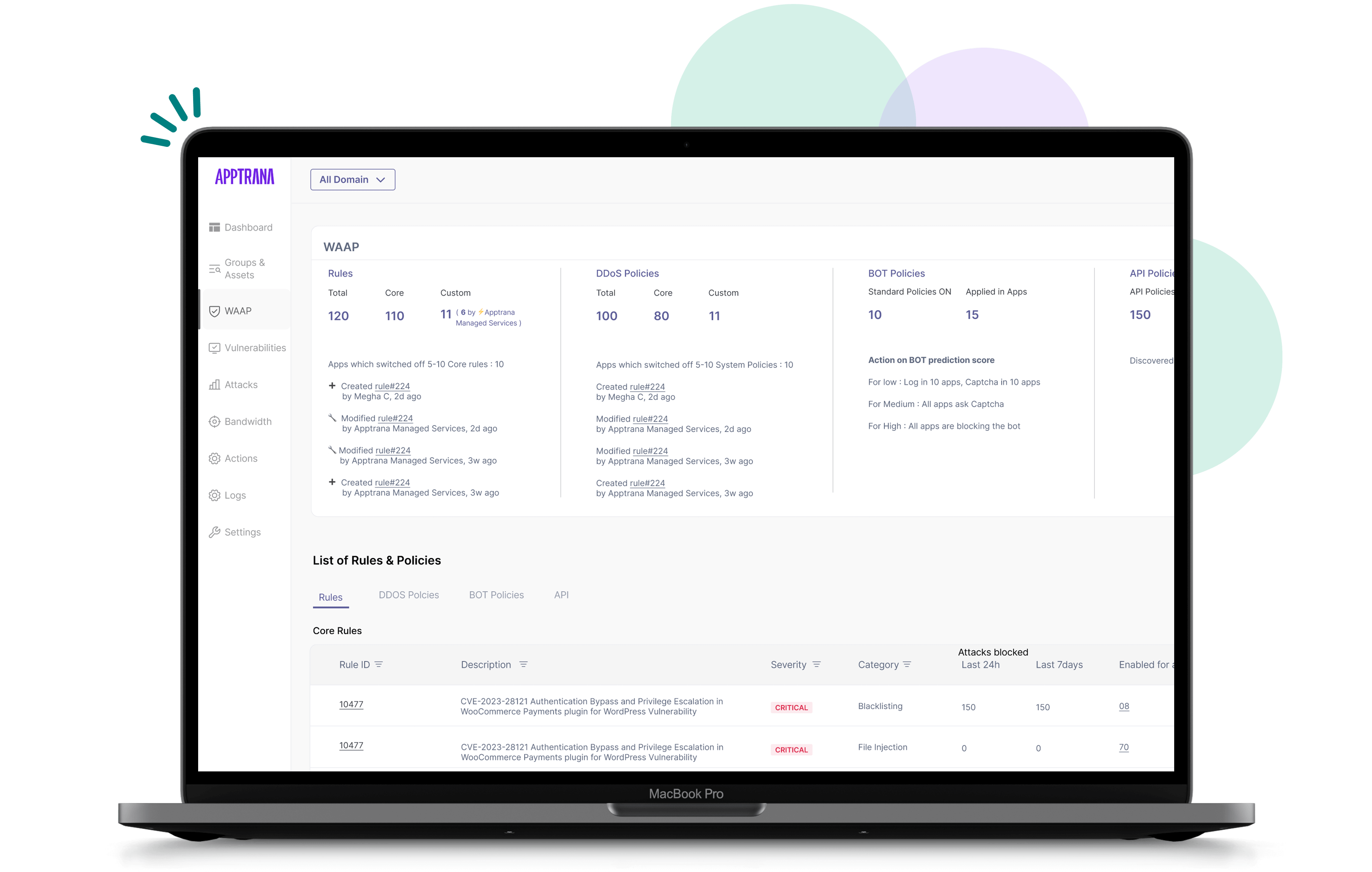
Recognized by leading industry analysts and organizations worldwide

Customer's Choice For 3 Years in a Row

#1 Security Product Company of India

Technology Partner Award Winner

Innovation for a Smarter Future

India's Fastest Growing Tech Companies
Complete protection for your applications and APIs